Protecting Your Digital Assets: A Comprehensive Guide to Cybersecurity
The purpose of this document is to provide individuals and organizations with a detailed understanding of the various aspects of cybersecurity, including the threats, vulnerabilities, and best practices for protecting their digital assets. The white paper aims to educate readers about the importance of cybersecurity in today's digital space and to help them develop a comprehensive cybersecurity plan that meets their unique needs and constraints. In the cybersecurity market, this document will help companies identify and target the right customers by segmenting the market based on industry, size, maturity model, assessments, and other relevant factors. It also helps companies understand their target customers' needs and challenges and tailor their products and services accordingly.
Introduction
Cybersecurity is a critical concern facing individuals and organizations today. The rapid growth of technology and the increasing reliance on digital platforms have created new opportunities for criminals and hackers to target sensitive data and intellectual property. The consequences of a cyberattack can be devastating, including financial loss, reputational damage, and legal liability. To protect against these threats, it is essential to have a comprehensive understanding of cybersecurity and to develop a vigorous cybersecurity plan that addresses unique essentials and vulnerabilities.
Importance of Cybersecurity
Cybersecurity is essential in today's digital era, as it plays a crucial role in protecting individuals, businesses, and governments from various cyber threats. Cyberthreats, such as hacking, malware, Bot-defense, and phishing attacks, can cause significant damage, including financial loss, reputational damage, and the loss of sensitive information. Cybercriminals can exploit vulnerabilities in computer systems and networks without adequate cybersecurity measures, compromising personal and financial information and disrupting critical infrastructure such as power grids, authentication intelligence, transportation systems, and communication networks.
Effective cybersecurity measures can help prevent cyberattacks and mitigate the damage caused by successful attacks. This includes implementing strong passwords, regularly updating software and security systems, educating employees on cybersecurity best practices, and monitoring networks for suspicious activity. Overall, cybersecurity is crucial in today's digital age to ensure the protection of sensitive information, critical infrastructure, and the continued functioning of society.
Cybersecurity Threats
Cybersecurity threats are any malicious activity that targets computer systems, networks, and other digital devices. These threats are constantly evolving, and the risk of a cyberattack is increasing rapidly. Some of the common current cybersecurity threats include:
It's important to note that cybersecurity threats are constantly evolving, and new threats may emerge in the future. Organizations and individuals should stay informed about the latest threats and proactively protect their systems and data.
Instances of high-profile cyber-attacks and their impact on organizations and individuals
有几个知名的网络攻击in recent years that have impacted both organizations and individuals. Here are some examples:
• SolarWinds hack: In 2020, a massive cyber-attack targeted SolarWinds, a software provider for government and corporate networks. The attackers compromised SolarWinds Orion software, allowing them to gain access to multiple government agencies and organizations, including the U.S. Treasury Department and the Department of Homeland Security. This attack compromised sensitive data and highlighted the vulnerability of supply chains.
• Colonial Pipeline cyber-attack: In May 2021, a cyber-attack targeted the Colonial Pipeline, a major fuel pipeline operator in the U.S. The attack disrupted the company's operations, leading to gas shortages and price increases across the East Coast. This attack highlighted the potential impact of cyber-attacks on critical infrastructure.
• JBS Foods ransomware attack: In June 2021, JBS Foods, one of the largest meat processors in the world, suffered a ransomware attack that impacted its operations in the U.S., Canada, and Australia. The attack disrupted the company's supply chain and highlighted the potential impact of cyber-attacks on the food industry.
These high-profile cyber-attacks demonstrate the potential impact of cyber threats on organizations and individuals and the importance of taking cybersecurity seriously.
Key Insights from GVR's Independent Survey across IT Decision-makers & Cybersecurity Professionals
•Two Thirdof IT professionals across the financial services industry reported an increase in cyber-attacks in the past year. The top cybersecurity priorities for these organizations were network security, threat detection, and endpoint security.
•6 out of 10small and medium-sized businesses (SMBs) had experienced a data breach in the past 12 months. The top cybersecurity challenges for SMBs were lack of resources, lack of knowledge, and the complexity of cybersecurity solutions.
•Around 70%of cybersecurity professionals believed that artificial intelligence and machine learning would play a significant role in improving cybersecurity in the next 3-5 years. The top cybersecurity technologies being used by organizations were firewalls, intrusion detection/prevention systems, and security information and event management (SIEM) systems.
•More than 60%of IT decision-makers in the healthcare industry had increased their cybersecurity budgets in the past year. The top cybersecurity priorities for these organizations were data protection, threat detection, and compliance with regulations such as HIPAA.
•6 out of 10cybersecurity professionals believe that there is a shortage of skilled cybersecurity professionals. The top cybersecurity skills in demand are threat analysis, network security, and cloud security.
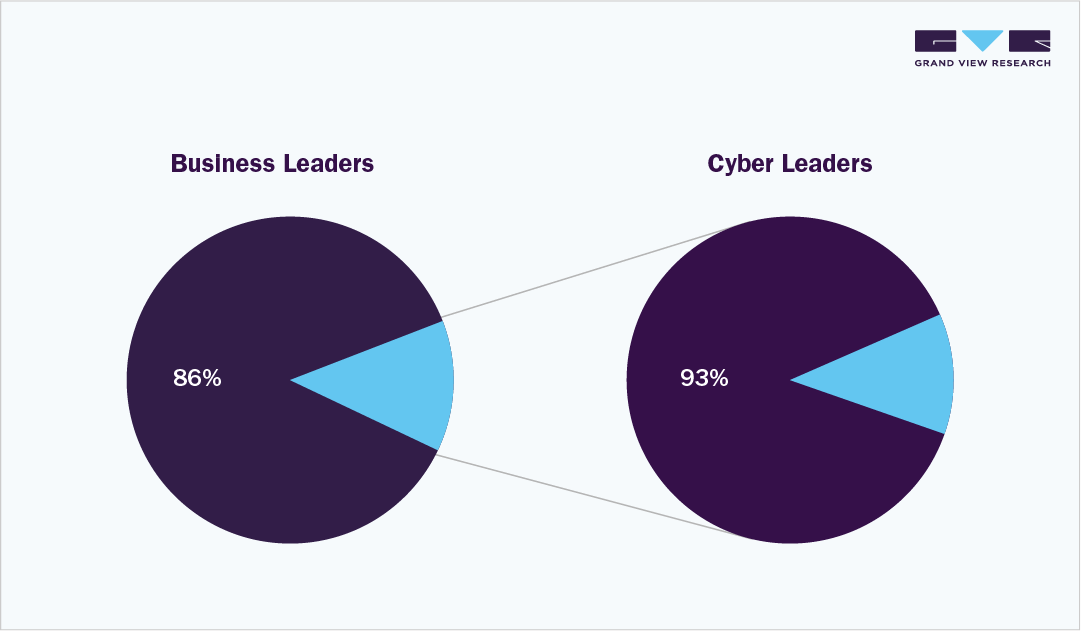
• Business and cyber-Leaders believe global geopolitical instability is moderate or very likely to lead to catastrophic cyber events in the next 2 years.
• In comparison with cyber leaders, business leaders are substantially more likely to strongly agree that more sector-wide regulatory enforcement would increase cyber resilience.
Staying Ahead of the Curve: An Analysis of Competitive Differentiators in Cybersecurity
According to Grand View Research, the global cyber security market was valued at USD 202.72 billion in 2022 and is projected to expand at a compound annual growth rate (CAGR) of 12.3% from 2023 to 2030.
The cybersecurity market is constantly evolving and growing, driven by the increasing frequency and sophistication of cyber threats. As more organizations shift to DX technology and platforms, and adopt cloud technologies, robust cybersecurity solutions become increasingly significant.
In this highly competitive market, vendors continually seek ways to differentiate themselves and gain a competitive advantage. One of the key competitive differentiators in the cybersecurity market is the ability to provide comprehensive solutions that cover all aspects, from threat detection and response to network and cloud security to identity and access management.
Other important competitive differentiators in the cyber market include the ability to provide tailored solutions that meet the unique needs of different organizations and industries and provide strong customer assistance and offerings. Moreover, the increasing focus on compliance and regulatory requirements is a key factor that influences the cybersecurity market. As more organizations must comply with data privacy and cyber security regulations, vendors that can provide solutions that meet these requirements have a competitive advantage.
The COVID-19 pandemic has significantly impacted the adoption of cybersecurity solutions as more organizations shift to remote work and digital platforms. With many employees now working from home and accessing corporate networks from personal devices, the need for robust cybersecurity solutions has become even more critical. The pandemic has also increased cyber threats, with hackers seeking to take advantage of the disruption and vulnerabilities created by the pandemic.
此外,网络安全的攻击阶段pandemic are divided into four main stages. The first stage was characterized by phishing and social engineering attacks, sent pretend emails and messages to users, enticing them to click on malicious links or provide sensitive information. The second stage saw increased remote access exploitation, with cybercriminals targeting vulnerabilities in remote access tools to gain unauthorized access to company networks and data. The third stage was marked by a surge in ransomware attacks, particularly targeting healthcare organizations, government agencies, and businesses. Finally, the fourth stage witnessed increased targeting of IoT devices and cloud-based infrastructure as cybercriminals sought to exploit these systems' vulnerabilities to steal data or launch attacks. To alleviate the risks associated with these hacking phases, individuals and organizations must remain vigilant and take steps to secure their networks and devices, including implementing strong passwords, enabling multi-factor authentication, and regularly updating software. This has further highlighted the need for strong cybersecurity solutions to protect against these threats. As a result, there has been a significant increase in demand for cybersecurity solutions since the pandemic. Vendors that offer comprehensive solutions that cover all aspects of cybersecurity and tailored solutions for different industries and organizations have seen strong growth during this time.
总的来说,网络安全市场高度竞争itive and constantly evolving, with vendors seeking ways to differentiate themselves and provide solutions that meet the evolving needs of their customers. The ability to provide comprehensive solutions, tailored solutions, strong customer support, and compliance with regulatory requirements are all important competitive differentiators in this market. According to the Grand View Research, the cyber security market is estimated to reach 500.70 billion by 2030.
GVR Perception
GVR is offering a GlobalCyber Security Marketreport which provides an in-depth analysis of the market dynamics, Industry sizing, trends, landscaping, opportunities, and challenges. The report highlights that the increasing frequency and sophistication of cyber-attacks drive the growth of the cybersecurity market. The rise in remote work and the increasing use of mobile devices and social media have also created new security challenges that require advanced cybersecurity solutions. The report also states that the demand for cloud-based security solutions is increasing due to the growing adoption of cloud computing and the need for scalable and flexible security solutions.
The report covers various cybersecurity market segments, including component, type, deployment mode, organization size, and end-user industry. The report also provides a regional market analysis covering North America, Europe, Asia Pacific, Latin America, the Middle East, and Africa. The report identifies North America as the largest regional market for cybersecurity, followed by Europe and Asia Pacific. The Asia Pacific region is expected to witness the highest growth rate due to the increasing adoption of digital technologies and the growing awareness of the need for cybersecurity.
The Grand View Research market report on the cybersecurity market provides valuable insights for businesses, investors, and other stakeholders interested in the industry.
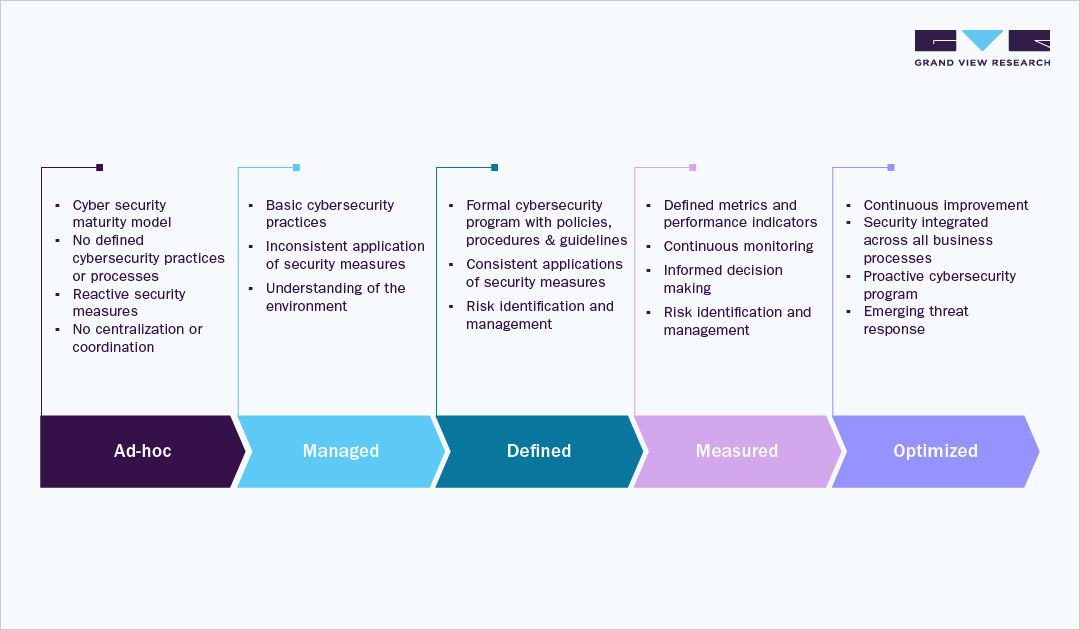
Cyber Security Maturity Model
GVR's maturity model on cybersecurity refers to a framework that assesses and benchmarks the level of maturity of an organization's cybersecurity capabilities. Such a model helps organizations to understand their current state of cybersecurity readiness and identify areas for improvement. Here's a maturity model for cybersecurity:
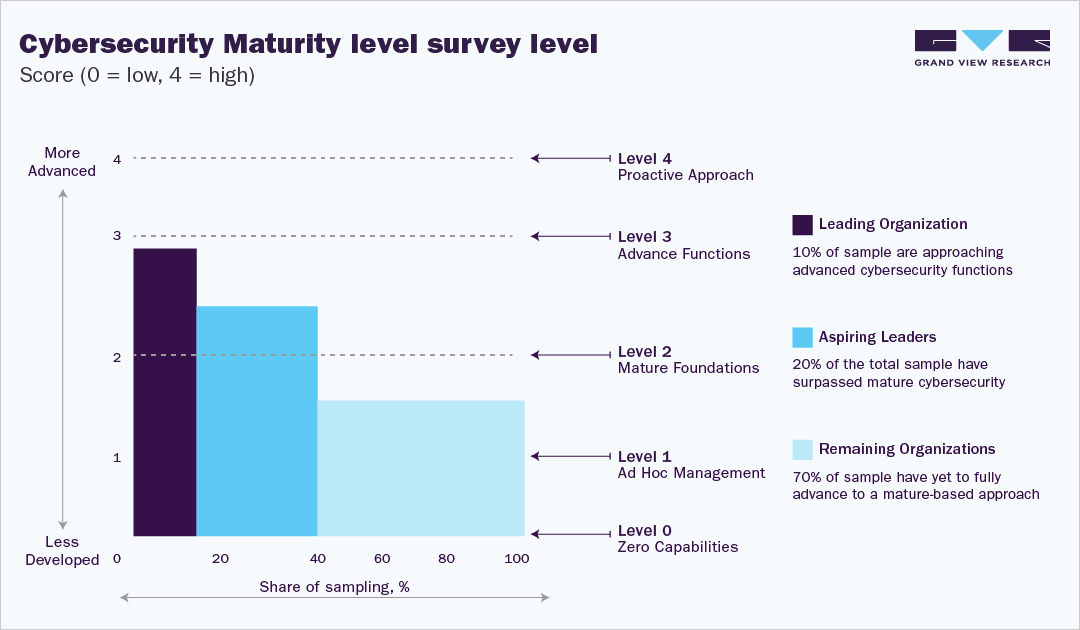
Cybersecurity Maturity level survey level,score (0 = low, 4 = high)
CISCO Services: Cyber security solutions
Cisco Systems, Inc. is a leading provider of cybersecurity solutions for organizations of all sizes. With over 30 years of experience in the networking and cybersecurity industry, has a deep understanding of the evolving threat landscape and the tools and technologies needed to protect against cyber threats. One key factor contributing to Cisco's stability in the cybersecurity market is innovation and continuous product improvement. Cisco's stability in the cybersecurity market is also reflected in its strong financial position and market share. The company is ranked as one of the top providers of cybersecurity solutions by industry analysts. It has a large and loyal customer base that relies on its products and services to protect its sensitive data and assets. Furthermore, end-user organizations generally have an optimistic perception of Cisco's cybersecurity solutions. It has a long-standing reputation for innovation, quality, and reliability and is recognized as a trusted provider of cybersecurity solutions for organizations of all sizes.
Customer Drivers to Adopt Cyber Security
在当今越来越多的数字世界,cybersecurity threats are becoming more prevalent and sophisticated, making it essential for organizations to adopt cybersecurity measures to protect their sensitive data and business operations. There are several customer drivers that may motivate organizations to adopt cybersecurity measures. Compliance requirements, such as those imposed by industry regulations or government mandates, are a common driver for cybersecurity adoption. Organizations may also be motivated by the need to protect sensitive data from unauthorized access or theft, maintain business continuity, or protect their reputation and brand from cybersecurity breaches. Additionally, investing in cybersecurity measures can save costs in the long run by reducing the risk of costly security breaches or data loss. Finally, demonstrating strong cybersecurity measures can differentiate organizations from competitors and instill customer confidence, leading to a competitive advantage. Organizations can adapt their cybersecurity strategy to effectively protect their operations and data by understanding their specific drivers for cybersecurity adoption.
Defending Against Cyber Threats: Key Recommendations for End Users in the Cybersecurity Market
With the increasing prevalence and sophistication of cyber threats, it's essential for end users to adopt effective cybersecurity measures to protect their sensitive data and assets. GVR recommendations for end-users of cybersecurity solutions to help them make informed decisions:
Firstly, it is important to conduct a risk assessment to identify sensitive data and critical assets that need protection and assess the risks and vulnerabilities that could lead to a cyber-attack. Moreover, end-users should identify the specific security requirements necessary to protect their data and assets, such as access controls, encryption, and network security measures.
此后,重要的是要研究可用cybersecurity solutions that meet specific needs and requirements, considering cost, ease of implementation, and ease of use. GVR cybersecurity experts or consultants provide valuable insights and recommendations on any aspects of cyber security. Implementing a layered approach to cybersecurity, including multiple layers of protection such as firewalls, anti-virus/anti-malware software, and intrusion detection/prevention systems, is essential. End-users should also train their employees in best practices, such as password management, recognizing phishing attempts, and reporting suspicious activity.
In conclusion, it's important to regularly monitor and update cybersecurity solutions to ensure they are effective against new and evolving threats. By taking a proactive approach to cybersecurity, end-users can protect their sensitive data and assets and reduce the risk of cyber-attacks.
To schedule a free market intelligence database demo, please complete the form below:
Service Guarantee
-
Insured Buying
This report has a service guarantee. We stand by our report quality.
-
Confidentiality
Your transaction & personal information is safe and secure.
-
Custom research service
Design an exclusive study to serve your research needs.
-
24/5 Research support
Get your queries resolved from an industry expert.